hooareyoo™ Consultancy
Never has security been more relevant for businesses than in the digital age where sensitive corporate information can be accessed and shared so easily and efficiently.
At hooareyoo™ we offer companies a unique approach in assessing the strengths and weaknesses within their procedural and relational security by utilising our skills and experience in intelligence gathering, risk assessment and personality profiling. What sets us apart from anyone else is the data we use to undertake our analysis is derived from the actual day-to-day activity of the key personnel that directly impact upon your security.
For example, relational security is often summarised as about having a safe and secure relationship with your employee base, but it’s so much more than that. It concerns the knowledge and understanding you have of your staff and the way this information is used to manage security and risk.
Through our team of professional consultants with experience in clinical psychology, law enforcement, security, counter terrorism, insider threat and employment law, hooareyoo™ can utilise the insight gained through its profiling techniques to assist you in building robust policies and procedures for your business.
Every business is unique, and we deliver a bespoke solution for each project based on a range of criteria, including size of employee base and key corporate objectives. Essentially, our expertise in security will enable you to identify, assess, manage and mitigate risk.
Typically, our approach has four stages:
- Scoping
- Discovery
- Education
- Implementation
1. Scoping
How relevant is this for your business?
Ahead of any engagement, we engage in a precursory scoping exercise to establish the relevancy of these topics, and, if applicable, to focus the formal sessions onto key risks that are present for that business at that time. This is free of charge.
2. Discovery
Presentation & Workshop: Relational Security Review & Assessment
Designed specifically for your business requirements, this 1-2 day workshop will involve formal presentations by our team across the subject of security best practice. We then facilitate interactive group exercises and case studies to identify the relevance of each of the key principles presented and to determine high risk areas by rank of importance.
The session will cover:
- Business Vulnerability
- Insider Threat
- Personality Traits – The Big 5
- The Psychological Contract and Optimal Foraging Theory
- Understanding Online Behaviour
- Digital Open Source Information
3. Education
Organisational Learning: applying these findings to the business
This stage will support key business personnel in embedding the insight secured in the Discovery stage across the business. We work with you in reviewing your business’s structures, processes, teams and personnel, to identify behaviours and to advise on how to implement measures that mitigate identified risk and help prevent further security issues arising.
4. Implementation
Establishing best practice
Following on from the organisational review and assessment, we will provide a detailed and structured method for the business to begin using the hooareyoo™ products and services to complete the security review.
Why use hooareyoo™?
- Promotes robust, defensible and informed decision-making
- Encourages an enhanced understanding of team dynamics and identity
- Provides a significant management step to mitigate key business risks
- Professionalises an area that is widely misunderstood or ignored
- Evidences due diligence and accountability by using professional industry experts
- Supports critical infrastructure and associated services
- Delivers legitimate, highly credible insight into individual and team behavioural traits
- Secures a competitive advantage by addressing key issues ahead of others
- Offers support to staff in highly sensitive roles
- Creates organisational deterrence of risk behaviours by overtly addressing causes
Who Would Use hooareyoo™?
Our Security Advisory Service is relevant for any business that can identify with any of the following staff roles or behavioural traits:
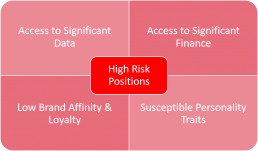
Below are some examples of where our services can be utilised:
- Hotel & Leisure Groups: high turnover staff roles with low brand affinity
- Retail: internal risks of theft from low affinity roles
- Education: digital due diligence around e-Safety in recruitment
- Banking: low turnover of high value staff with access to data
- Military: high pressure roles with high access to critical data
- Critical Infrastructure: low turnover of high value staff with access to data